
Network Security
Virtualization security
Endpoint security
Mobile Security
Electronic Signature


Reliable software and hardware complex for trusted load of operating system
Integration into the Secret Net Studio management server creates economies in terms of the operation and status monitoring of a large number of Sobol products.
Critical data stored in an independent memory module does not allow an attacker to bypass the protection system, even if software is compromised.
A solution leader in its class, Sobol has the highest level of reliability and the largest number of equipment tested for compatibility.
Sobol is included in the list of mandatory equipment for the use of cryptographic information protection tools for class KC2 and higher.
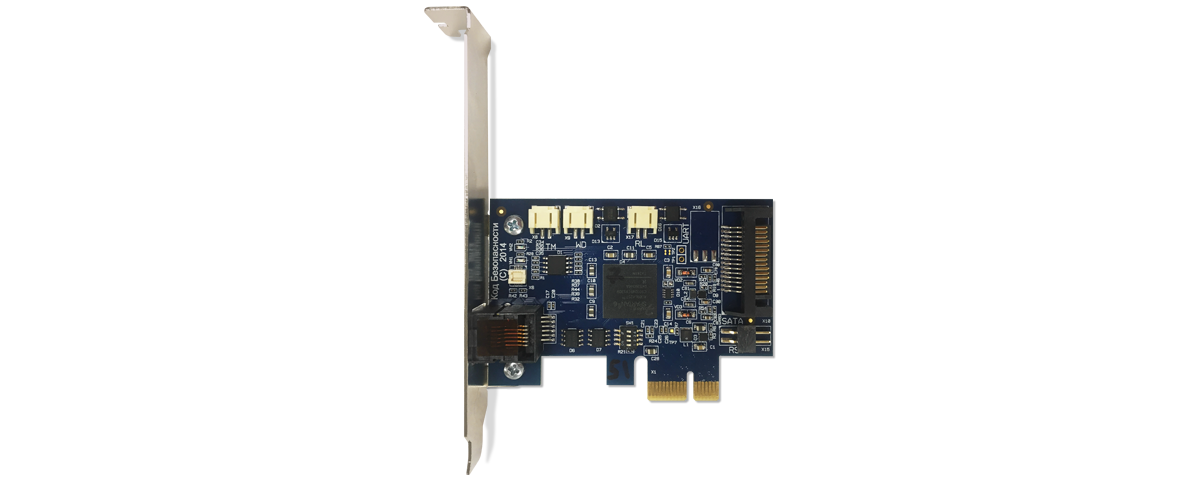
| Size: | 57 х 80 mm |
| Interface: | PCI Express RJ12 external reader connector for an iButton device Connector for iButton sensor internal reader Connection cable for watchdog timer mechanism |
| Compatible personal identifiers: | iButton DS1992, DS1993, DS1994, DS1995 and DS1996 iKey 2032 USB keys eToken PRO USB keys eToken PRO (Java) USB keys eToken PRO USB cards via USB reader Athena ASEDrive IIIe USB V2 Rutoken S and Rutoken S RF USB keys |
| Certified by: | FSTEC FSB the Ministry of Defense |
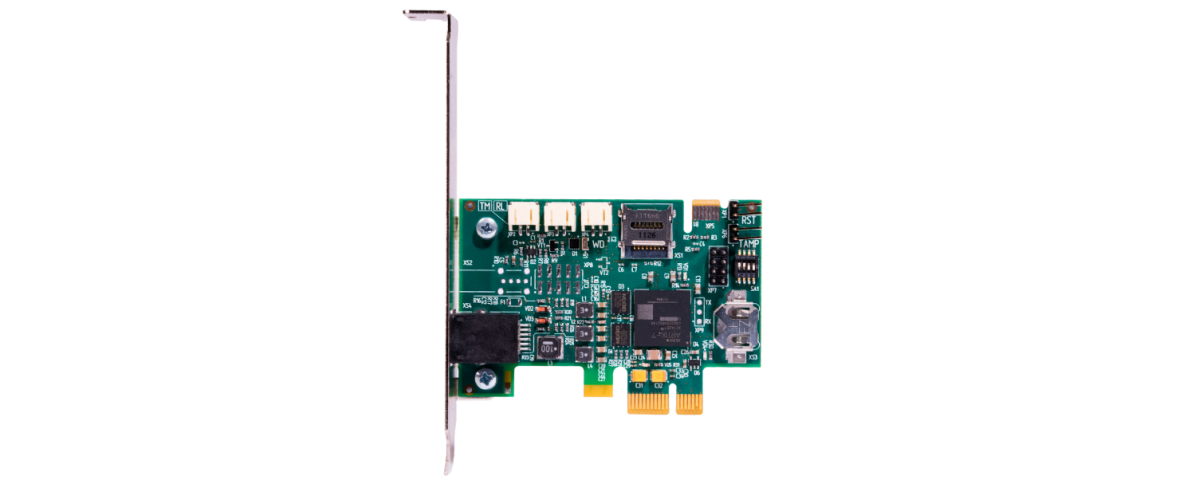
| Size: | 57,5 х 80,7 mm |
| Interface: | PCI Express RJ12 external reader connector for an iButton device Connector for iButton sensor internal reader |
| Compatible personal identifiers: | iButton DS1992, DS1993, DS1994, DS1995, DS1996, SC Button 92 USB keys: eToken PRO, eToken PRO (Java), ESMART Token 64k, Rutoken (S), Rutoken RF, Rutoken 2151, Rutoken ECP 2.0/3.0, Rutoken Lite, Rutoken ECP 2.0 2100 (RF), JaCarta-2 GOST, JaCarta-2 PKI/GOST, JaCarta SF/GOST, Guardant-ID, Guardant-ID 2 Smart cards: Foros, eToken PRO, eToken PRO (Java), JaCarta-2 GOST, JaCarta-2 PKI/GOST, Rutoken ECP 2.0, Rutoken 2151, Rutoken Lite |
| Certified by: | FSTEC the Ministry of Defense |

| Size: | 26 x 30 mm |
| Interface: | Mini PCI Express Connection of an internal or external reader for iButton Identifiers (via an extra adapter) |
| Compatible personal identifiers: | iButton DS1992, DS1993, DS1994, DS1995 and DS1996 iKey 2032 USB keys eToken PRO USB keys eToken PRO (Java) USB keys eToken PRO USB cards via USB reader Athena ASEDrive IIIe USB V2 Rutoken S and Rutoken S RF USB keys |
| Certified by: | FSTEC FSB the Ministry of Defense |

| Size: | 30 x 22 mm |
| Interface: | М.2 type 2230-D4-A-E Connection of an internal or external reader for iButton Identifiers (via an extra adapter) |
| Compatible personal identifiers: | iButton DS1992, DS1993, DS1994, DS1995 and DS1996 iKey 2032 USB keys eToken PRO USB keys eToken PRO (Java) USB keys eToken PRO USB cards via USB reader Athena ASEDrive IIIe USB V2 Rutoken S and Rutoken S RF USB keys |
| Certified by: | FSTEC the Ministry of Defense |
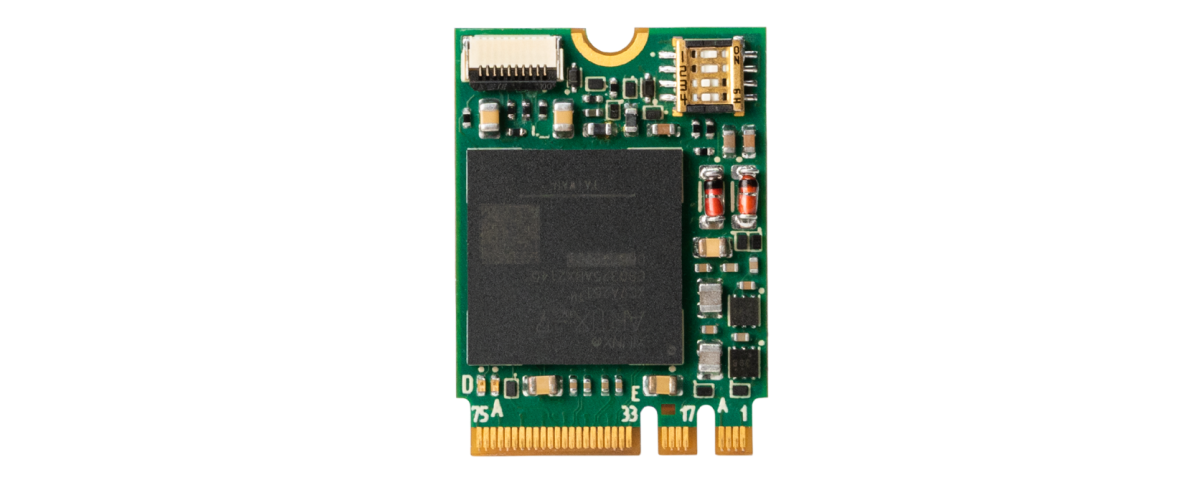
| Size: | 22 х 30 mm |
| Interface: | М.2 type 2230-D4-A-E Connection of an internal or external reader for iButton Identifiers (via an extra adapter) |
| Compatible personal identifiers: | iButton DS1992, DS1993, DS1994, DS1995, DS1996, SC Button 92 USB keys: eToken PRO, eToken PRO (Java), ESMART Token 64k, Rutoken (S), Rutoken RF, Rutoken 2151, Rutoken ECP 2.0/3.0, Rutoken Lite, Rutoken ECP 2.0 2100 (RF), JaCarta-2 GOST, JaCarta-2 PKI/GOST, JaCarta SF/GOST, Guardant-ID, Guardant-ID 2 Smart cards: Foros, eToken PRO, eToken PRO (Java), JaCarta-2 GOST, JaCarta-2 PKI/GOST, Rutoken ECP 2.0, Rutoken 2151, Rutoken Lite |
| Certified by: | FSTEC the Ministry of Defense |
To operate the Sobol software-hardware system, a safe environment without the typical vulnerabilities is required, including vulnerabilities about which information can be found in open source materials. A study of computer software and hardware (including a study of BIOS system software) must be run, in order to ensure the absence of hardware and software mechanisms which are incompatible with Sobol and would therefore lead to computer or Sobol system malfunction, or compromise the security of the data/information being protected.
The volume and depth of the system’s research is determined by how secret (confidential) the information under protection is, the intruder model adopted, and the seriousness of the threat to confidentiality, as described in the corresponding requirements. The body of the workstation on which Sobol is installed must be protected from meddling and/or unauthorized access to its internal components.
| Operating system | Guaranteed compatibility with Windows OS versions:
Guaranteed compatibility with Linux OS versions:
|
| File system | FAT16, FAT32, NTFS, EXT2, EXT3, EXT4 |
| RAM | As per requirements of the OS Installed on the PC |
| HD (free space) | Minimum - 50 MB |
| Optical drive | CD/DVD-ROM The requirement is not mandatory if a common access network resource with Sobol software is available |
| System board | Available system bus open slot:
Implementation of the watch dog timer mechanism at least 1 of the following requirements:
|
| Operating system | Guaranteed compatibility with Windows OS versions:
Guaranteed compatibility with Linux OS versions:
Guaranteed compatibility with Unix OS:
|
| File system | NTFS, FAT32, FAT16, UFS2, UFS, EXT4, EXT3, EXT2 |
| RAM | As per requirements of the OS Installed on the PC |
| HD (free space) | Minimum - 50 MB |
| Optical drive | CD/DVD-ROM The requirement is not mandatory if a common access network resource with Sobol software is available |
| System board | Available system bus open slot:
Implementation of the watch dog timer mechanism at least 1 of the following requirements:
|
| Operating system | Guaranteed compatibility with Windows OS versions:
Guaranteed compatibility with Linux OS versions:
Guaranteed compatibility with Unix OS:
|
| File system | NTFS, FAT32, FAT16, UFS2, UFS, EXT4, EXT3, EXT2 |
| RAM | As per requirements of the OS Installed on the PC |
| HD (free space) | Minimum - 50 MB |
| Optical drive | CD/DVD-ROM The requirement is not mandatory if a common access network resource with Sobol software is available |
| System board | Available system bus open slot:
Implementation of the watch dog timer mechanism at least 1 of the following requirements:
|
Information contained in these documents may be changed by the developer without special notice; such changes do not violate the developer’s obligations to the user.
Administrator’s Manual. Getting Started.
Information on how to quickly start working with Hardware Trusted Boot Module Sobol.
Administrator’s Manual. Setup and Operation.
Information that administrators need in order to install, configure and use the product.
Administrator’s Manual. Sobol Software.
Information about setup and operation of Sobol software.
Information which users need to work with Sobol.
Administrator’s Manual. Getting Started.
Information on how to quickly start working with Hardware Trusted Boot Module Sobol.
Administrator’s Manual. Setup and Operation.
Information that administrators need in order to install, configure and use the product.
Administrator’s Manual. Sobol Software.
Information about setup and operation of Sobol software.
Information which users need to work with Sobol.